Being able to tell an AI to build you a website and actually get a website can seem like magic. For digital agencies, using AI to do a web developer’s job can reduce costs and expedite the production of digital deliverables. However, letting AI run the magic show unsupervised - a practice dubbed “vibe coding” - will have you pull a hat out of a rabbit in front of a live audience - unexpected, messy, and not what the audience signed up for.
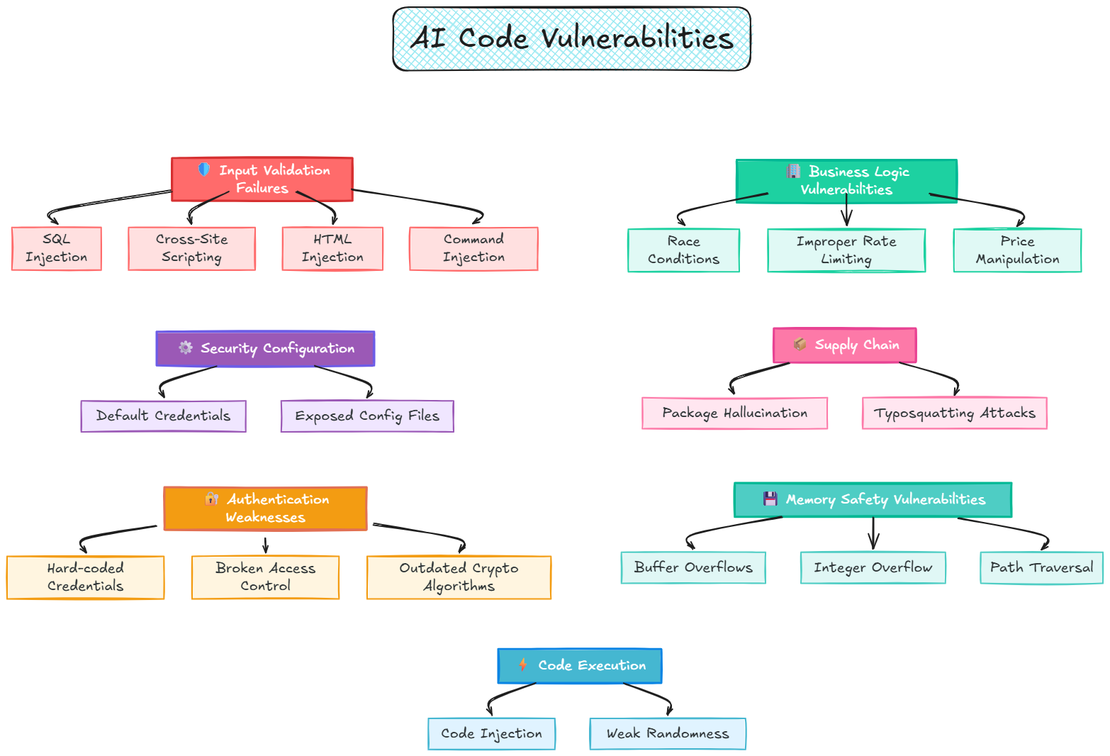
In practice, this means that hiding behind the curtain of your vibe-coded websites could be severe security vulnerabilities. As
much as 45% of the code generated by various AI tools fails security tests and introduces OWASP Top 10 vulnerabilities.
Before we discuss the security risks and vulnerabilities that vibe coding can conjure, let’s talk about what vibe coding actually is, and how it differs from responsible AI-assisted development or mature no-code/low-code platforms.
Vibe coding for websites: Is it ready yet?
Vibe coding (or vibecoding) is a recently-coined term for the practice of writing code, producing web pages, or creating apps by telling an AI in your own words what you want, and accepting whatever the model generates with no developer oversight or interaction with code. To be a “vibe coder”, you don’t need to learn how to write or even read software code syntax. But unlike low-code/no-code website builders or application platforms, vibe-coded products are not built within existing guardrails or atop human-managed infrastructure.
Vibe coding trades traditional software processes for speed, and replaces coding skills with stylistic intent and “shipping by prompt”. For example, you can type in “Create an elegant landing page for a SaaS company with a signup flow, analytics, and pricing tiers,” and the model will write the HTML/CSS/JS, pick dependencies and third-party resources, and make guesses as it does.
The trouble with vibe-coded websites
For digital marketers, vibe coding can feel like a magical shortcut to faster and cheaper shipping of client websites, with instant iterations and no need to deal with all the technical stuff in the way of publishing multiple client sites fast. It can enable an account manager or design lead to prompt an AI website builder or chat-driven copilot to scaffold webpages, wire forms, integrate plugins, and publish to the web. And it all happens without the normal process of website development from requirements, through architecture, reviewing, testing, and publishing.
Part of the magic of vibe coding is in the fact that decisions related to information and infrastructure security, web performance, accessibility, and maintenance are handled fully by the AI model. That magic is also the reason vibe coding introduces multiple issues and hidden liabilities. When the “how” of website building is guessed by a statistical model, you’re going to get mismatched plugins and permissions, leaky forms, brittle auth, unexpected SEO issues, and unclear ownership of the code and the (many) fixes it needs after publishing.
Top 10 risks of vibe coding websites for marketing agencies
1. Code secrets & env leaks
Vibe-coded scaffolds often skip secret hygiene and over-share build artifacts. This is why we see API keys in client bundles, public .env, and unscoped third-party keys. These trends are echoed by “one in every five” sites built using popular vibe coding platforms (like Lovable, Bolt, Base44 and a dozen others) are leaking code secrets and the
45% insecure-code failure rate in GenAI pipelines.
2. Broken authentication & authorization
Prompts assemble routes and roles quickly but omit server-side checks, leaving “preview” and admin-ish paths exposed. This maps to
OWASP’s top web risk and mirrors the access
flaws researchers surfaced in Base44, a vibe coding platform acquired by Wix. A critical access-bypass flaw in the system allowed unauthorized users to register for private apps using unprotected API endpoints, giving anyone with some technical skills access to private enterprise applications and their data.
3. Prompt injection & insecure output handling
Vibe coding tools work as a kind of “black box” that does things behind the scenes to achieve the goals specified in your prompt. However, it can also perform other actions that were prompted by malefactors unbeknownst to you. When the model behind the chatbot or AI copilot consumes untrusted pages or files, it can ingest hidden texts prompting it to perform behind the scenes actions like exfiltrate data, send spam, or change settings (indirect prompt injection attacks).
This vulnerability persists across different types of code generation LLMs, with coding agents like Cursor IDE
showcasing how poisoned prompts could weaponize an AI coding agent. The vulnerability enabled remote‑code execution triggered by a single externally‑hosted prompt‑injection that silently rewrites ~/.cursor/mcp.json and runs attacker‑controlled commands.
Another related issue is
insecure output handling, when LLM output is rendered directly onto a page or passed to backend functions without proper validation/sanitization, opening the door to XSS/CSRF/SSRF attacks.
4. Classic web injection (XSS/SQLi/Template Injection)
Web vulnerabilities are typically introduced by careless developers, and are easily caught by code scanners in a proper CI/CD pipeline so they are never deployed to live environments. With vibe coding, there is no pipeline, so the classic web vulnerabilities infosec analysts have long forgotten are making a comeback. Shortcuts like “build me a login” or “render this comment” can quietly re-introduce 2005-era bugs because the AI model ships whatever works, not whatever’s secure.
5. CORS, headers, and storage misconfigurations
Vibe coding will leave the doors to your site wide open, with Access-Control-Allow-Origin: *, missing CSP/HSTS, and overly permissive S3/CDN settings. This can enable unauthorized parties to read your data, frame your pages, or scrape private files from your servers.
The perfect example of
vibe coding gone wrong at scale was the
Tea App data leak, where an exposed Firebase instance revealed approximately 72,000 images, including 13,000 government ID photos from user verification and 59,000 images from posts and messages. Some of the images contained EXIF data that made it possible to triangulate the location where they were taken. The fallout of this leak was immense, with the database of women’s profiles uploaded to the
notorious image board 4chan.
6. Supply chain & “slopsquatting”
Software supply chain security is thrown to the wind with vibe coding, letting the AI choose libraries and dependencies via hallucinated packages, giving room to a new type of cybersquatting attack — slopsquatting.
Slopsquatting is a supply-chain attack where attackers register made-up package names that AI tools hallucinate, so future AI-guided builds will install those malicious packages as if they were real.
Slopsquatting is a reliable attack vector for malefactors as,
according to one study, 19.7% of all AI-recommended packages didn’t exist. What is more worrying is that those non-existent packages tended to re-appear in generated code. In fact, 58% of hallucinated packages were repeated more than once across ten runs. This means that a majority of package hallucinations are not just random noise, but repeatable artifacts that malefactors can abuse.
Moreover, when an AI picks the libraries and plugins to run on your vibe-coded websites, and sets them to auto-update by default, you inherit whatever ails those packages tomorrow. It might be malicious code, or quiet updates that break the sites you’ve just shipped.
7. Privacy & consent failures (GDPR/CCPA/DPAs)
Vibe coding and vibe coding platforms don’t pay much attention to user privacy, consent, or the laws that demand brands take responsibility for the data their users share with them. Vibe coding site builders will gladly build you a website, but if you’re looking to comply with GDPR and CCPA, you will need to
bolt on a cookie banner manually, which may introduce issues of its own. So it’s not surprising that users of vibe coding platform Base44
have been asking for a native cookie popup in feedback and reviews.
8. Availability & abuse
Ungoverned and unmonitored websites are goldmines for spammers and fraudsters. A vibe-coded site that ships with a basic checkout page with no bot controls can be easily abused.
As
Stripe described in one instance, automated “card testing” flooded the payment endpoint with thousands of $0–$1 authorization attempts as cybercriminals checked the validity of stolen credit card details. If your vibe-coded ecommerce site becomes such an abuse hub, the payment provider will quickly flag and block such accounts. The result: genuine clients can’t pay, and the hosting bills spike from the traffic.
9. Multi-tenant & environment mix-ups
Vibe-coded sites are troublesome for hosting services and multi-tenant environments. It’s very easy for a vibe-coded site to have indexing turned on by default,
making Google index staging subdomains, and displacing production until a cleanup/deindex. In addition, the now patched
platform-wide flaw on Base44 demonstrated how shared infrastructure can expose many projects and clients at once.
10. Third-party & tag manager risk
Malefactors are getting increasingly creative in finding ways into your website, and careless vibe-coding introduces plenty like over-permissive GTM containers, rogue scripts, unreviewed pixels and malicious widgets.
For example, Google Tag Manager has been used in multiple credit-card theft
attacks on Magento stores. Malefactors encode JavaScript payloads with credit-card skimmers, and collect sensitive data entered by users during the checkout process to send to a remote server controlled by the attackers. In another case,
WordPress sites were hijacked and redirected to spam sites. The attacker injected a seemingly legitimate Google Tag Manager (GTM) script into the WP database with a container ID they controlled and simply took over.
Vibe coded websites can easily include such code, same as they often include hallucinated malicious package dependencies.
When the vibe is off: the business and operational impacts of vibe coding websites
Client campaign disruptions
Prompt-generated markup that violates platform policies and third-party tag issues (like GTM skimmers) cause disapprovals, rollbacks, and delayed releases while paid budgets idle. This derails launch calendars and burns trust with acquisition teams.
Measurement chaos
Environment mix-ups and XSS/templating bugs split traffic and corrupt events, breaking attribution and A/B test validity. In the EEA, mis-wired
Consent Mode v2 suppresses conversions and dulls smart bidding. Decisions drift because the data is no longer reliable.
Regulatory and contractual exposure
Pixels firing pre-consent and leaky forms create unlawful processing risk under GDPR/CCPA and show up in DPAs/MSAs as indemnity and remediation obligations. If skimmers or tags touch cardholder data, expect PCI-DSS scrutiny and payment-provider reviews even if you’re not the merchant of record. Legal teams escalate, fines hit the bottom line, scopes and costs expand, and all because of a single vibe-coded prototype gone live.
Direct financial losses
Leaked keys and permissive agents can rack up LLM, email, maps, and analytics overages, or exhaust rate limits mid-campaign. These hit margins immediately and often fall outside the original SOW.
Unauthorized changes & data exposure
Broken access controls, prompt-driven content injections, and third-party compromises translate into incident response and potential disclosure obligations. Your tech teams will spend nights/weekends on rollbacks and hotfixes, and paid work pauses while you fund triage.
Cross-client blast radius
Shared tokens, mis-scoped roles, or env bleed turn a single defect into a multi-account event. Ops will need to juggle parallel cleanups, stakeholder comms across clients, and combined legal exposure, all multiplying cost and stress.
Availability and performance degradation
Badly built pages with heavy/hostile tags and plugins slow the user experience, trigger mixed-content or “not secure” warnings, and destabilize forms/checkout. Then, Core Web Viral scores slide, and email/domain reputation and conversion drop. To make things worse, these issues often surface only after publishing and approval, hurting revenues and adding overhead to support and tech teams.
Brand, trust, SLA, and retention risk
Visible defacements, consent “theater” that unravels, or public incident notes bruise client and agency credibility. Uptime/response misses trigger SLA penalties and causes renewal friction and lost business. Even after remediation, reputational debt lingers and expands the scrutiny on every subsequent release.
How agencies can leverage AI safely
Vibe coding can often cause more trouble than its worth. That said, there are plenty of ways you can use AI-generated assets in your websites and workflows.
1. Prototype fast in low-risk sandboxes
- Vibe coding is a quick and dirty way to spin up flows, sections, and even content on staging/preview sites. To do so safely:
- Keep prototypes and AI-generated mockups isolated from live data and search engine bots.
- Never upload untested vibe-coded pages onto live, public facing servers.
- Block indexing with a
robots noindex meta tag or an
X-Robots-Tag header.
- Password-protect staging, and remember that robots.txt is not by any means a method of access control.
2. Test with agents
Instead of vibe coding, try vibe testing websites instead. You can aim an AI tester at staging (or even live pages) to crawl in search for broken links, copy issues, accessibility glitches, and simple usability problems that can be found before human review. You can pair this with Lighthouse
accessibility/SEO audits, the
W3C alt-text decision tree, and a
broken-link pass.
3. SEO & accessibility ops automation
AI is exceptionally good at generating content, and you don’t need to know code to use it for various tasks like generating page titles, meta descriptions, and bulk alt texts. With a human editor in the loop, this can help streamline content operations, especially if you instruct the bot to keep output aligned with
Google’s SEO Starter Guide and WCAG basics like the
W3C alt-text decision tree.
4. Scale content faster
Another way to leverage generative AI’s ability to create a lot of content quickly can be in expediting personalization and customization tasks. You can generate unique city/branch intros, FAQs, and GMB descriptions from a single template, draft localized pages and language variants, and then route to human editors for branding and accuracy validation. To make sure you don’t hurt SERPs or digital trust in the process, remember to
think of the people first.
5. Insights & reporting drafts
In addition to generating large volumes of content, AI also excels at processing data and turning it into actionable insights. You can use AI to turn GA4 and Search Console data into plain-English “what changed / what to do next” summaries for your clients.
Start with GA4
BigQuery Export or the
BigQuery transfer docs, and use the
Search Console Performance report for query/page insights.
A more professional vibe: Why you should partner with a security-first, AI-enabled website building platform
Vibe coding means trusting AI to make all the calls in building a website, which often results in code secrets leakage, broken auth, prompt-injection, supply-chain drift, and consent/tag issues. In the world of cybersecurity, vibe coding is not regarded as magical at all, and as justifiably earned the description “vulnerability as a service”.
Building websites with AI can only work if security, access controls, privacy, compliance and reliability are baked in. For marketing agencies charged with building websites for multiple clients, Duda
pairs integrated AI with enterprise guardrails so agencies can move fast without courting the failures we flagged.
Designed with marketing agency operations in mind, Duda features:
- Access & change controls: Robust user permissions and MFA/SSO keep client/staff access scoped, reducing the chance of unauthorized edits and admin-route exposure.
- Privacy & consent, by default: Built-in privacy pages, native cookie notifications, tracking toggles, and EU hosting options help you meet GDPR/CCPA expectations without bolt-on hacks.
- Resilience you can prove: AWS hosting, 99.5% uptime, DDoS mitigation, SSL/TLS, AES-256 at rest, automatic backups, and a
live status page keep launches stable and verifiable.
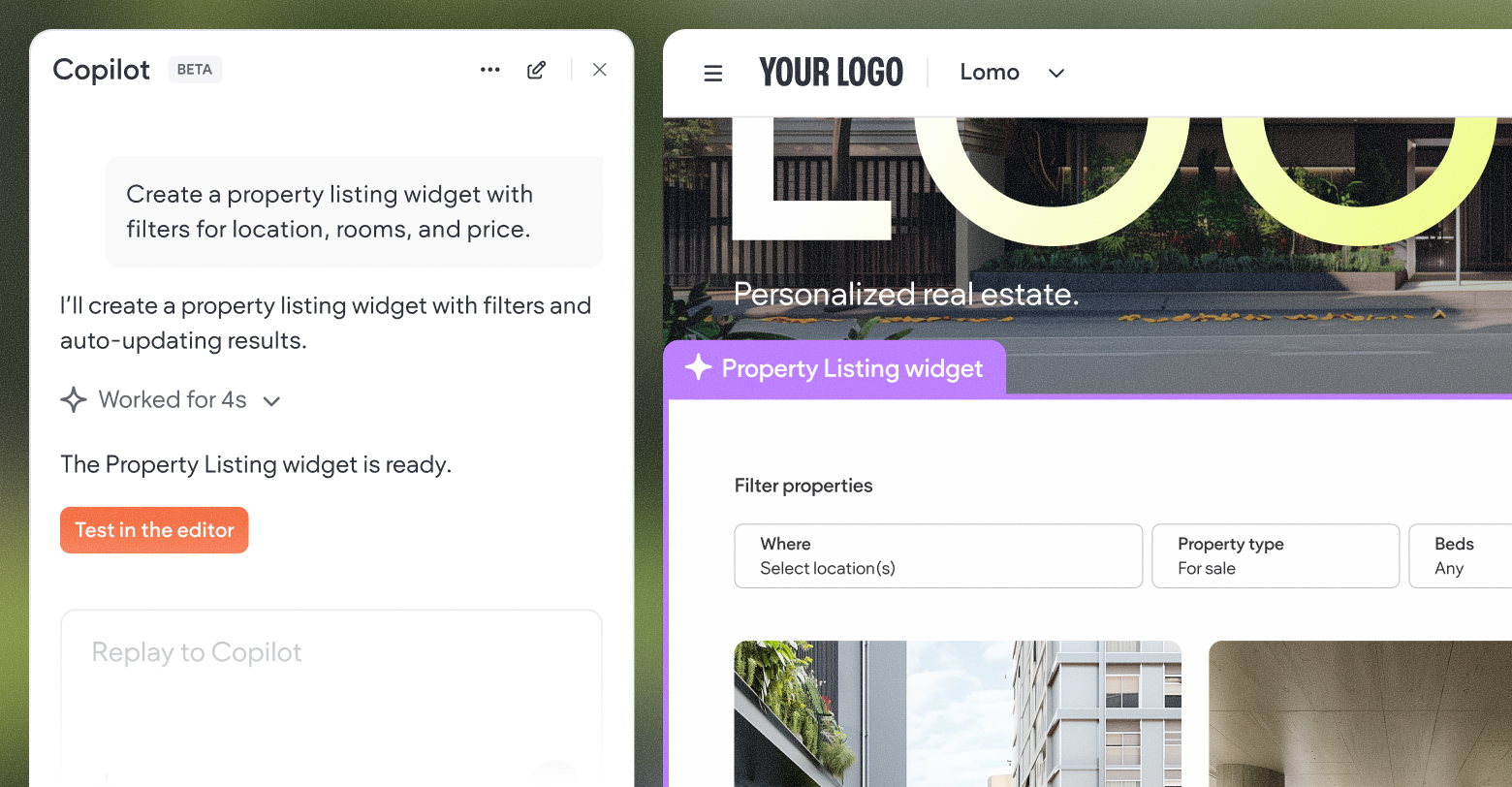
- AI website builder that fits pro workflows: AI Copilot and MCP connectors for conversational site management, as well as a dedicated AI Assistant for bulk titles/meta/alt text, content generation, and page recommendations. All with per-client AI permissions for governance.
- Unbreakable websites: Duda’s AI website building tools don’t generate code - so they don’t generate vulnerabilities. Instead, they employ the same production-ready components used in Duda’s visual website builder, enabling AI-accelerated creativity without the headaches of vibe coding.
If your agency is looking for the enchanted velocity of vibe coding with real-world client-safe controls and bulletproof security, schedule a demo with Duda.